The security of sensitive information has long been a major concern for organisations. With an increasing amount of data stored electronically, the challenge of keeping personally identifiable and commercially sensitive data secure has become even more pressing — especially with so much of it now stored and processed in the cloud.
And, while public sector data, financial records, customer information and confidential business reports were previously stored in secure facilities where physical access was restricted and closely monitored, in the digital age, vast amounts of data are continuously on the move.
These changes have seen the evolution of a security industry focused on ensuring confidential information is secure and can only be accessed by the people and systems authorised to do so.
Businesses are also realising and tapping into the value of the data they hold, with high-performance data processing driving whole new business models. With business data becoming more and more critical to operations, suddenly losing access to it would make it extremely difficult for many businesses to continue their activities.
The security challenges of high-performance workloads
High-performance computing is growing all the time, with the amount of data being extracted, transferred and stored increasing exponentially.
In addition to the sheer volume of data, high-performance workloads are complex, requiring a large number of nodes, distributed systems, and optimised configurations, which are tuned and tested for the specific business.
They must also deal with the added complexity that comes when data includes health records or financial information over different geographic regions, where local laws restrict the movement of certain types of information.
Add into the mix that these capabilities are increasingly provided in the cloud, and there are a number of extra considerations.
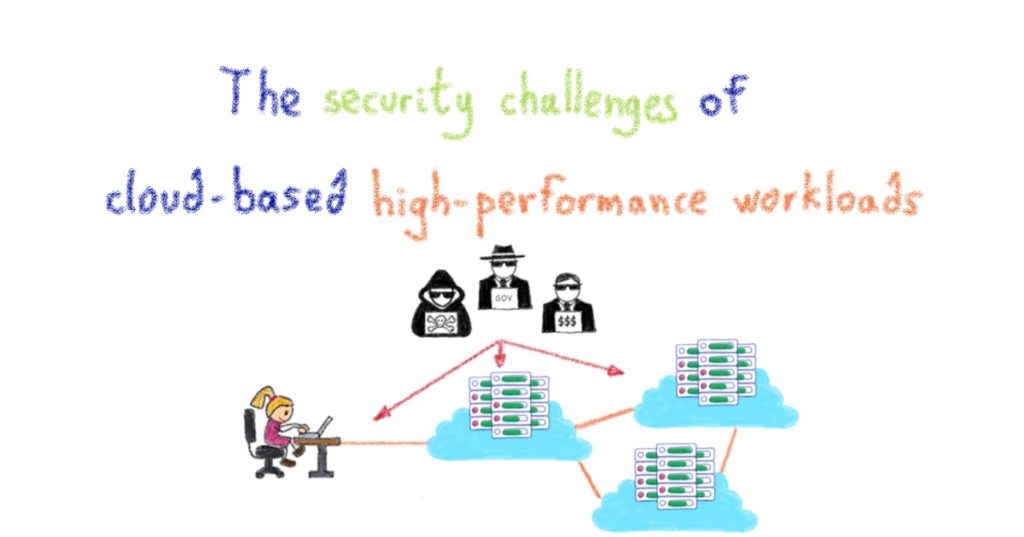
An expanded attack surface
With data being transferred to and from the cloud, as well as being processed and stored beyond the confines of organisation’s own IT infrastructure, there are more channels that malicious actors could use to intercept, disrupt or steal data.
Cloud providers’ data centres, which contain server hardware, network switches and IT tools, further expand this attack surface.
OVHcloud, for example, provides millions of public IP addresses across five continents and faces a constant battle to thwart attacks from hackers and criminal organisations hoping to profit from data theft, fraud and compromised systems.
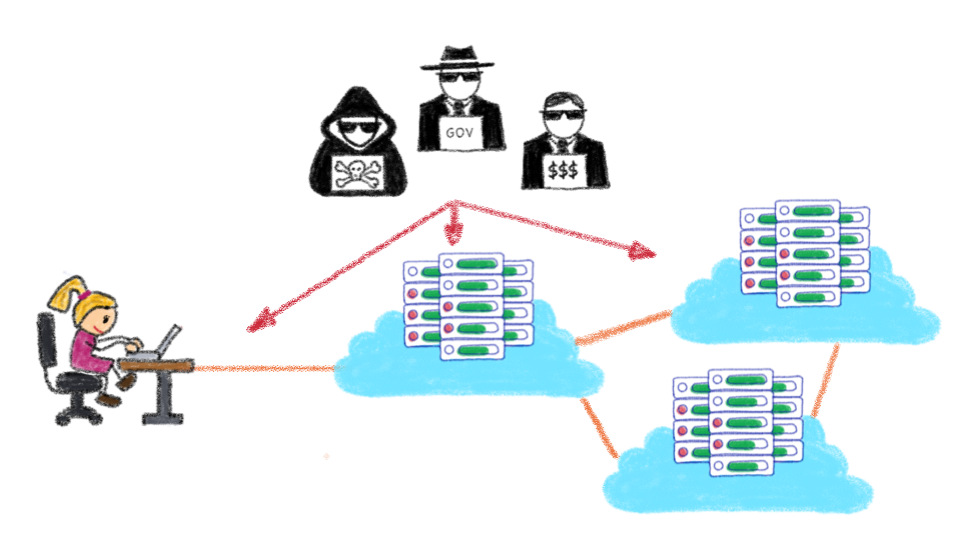
This larger attack surface means cloud-based data processing is more attractive to malicious individuals or groups conducting distributed denial of service attacks (DDoS), where they attempt to overload an application or network with too much information.
High-performance workloads require high availability and lots of compute power by definition, so can be particularly impacted by these types of attacks. Not only can DDoS attacked overwhelm servers, they can also affect the general speed of traffic on the network — another issue that could particularly impact high-performance workloads.
Protecting high-performance workloads
Malicious actors present a constant threat to customer data, and so cloud providers of high-performance capabilities must go above and beyond when it comes to protecting the information on their networks.
They need to follow security best practice, use the most reliable and tested technology, and abide by regulations set out by governments and regulators.
Decentralising the computing and running high-performance workloads on numerous servers at the same time, means a successful attack on a server is less likely to affect the high-performance environment.
It’s also important for organisations to put disaster recovery and business continuity capabilities in place, so mission-critical workloads can continue to safely and securely operate even if a security issue occurs.
Being aware of the combined security implications of high-performance workloads and the cloud, means organisations can plan the right approach and select the cloud provider that will best manage their risks.
