Written in collaboration with Mike Ferron-Jones from Intel
Our challenging cyberthreat environment has enterprises searching for new data protection, privacy solutions and best practices by their cloud providers. OVHcloud’s new Advance-6 Bare Metal Servers are equipped with 3rd Gen Intel® Xeon® Scalable Processors (formerly code-named “Ice Lake”) and Intel® Software Guard Extensions (Intel SGX). These unique technologies offer increased performance and leverage Confidential Computing for data privacy, regulatory compliance and stronger data protection.
Read this article to learn more about Confidential Computing and how you can benefit from these capabilities.
At the core of modern business transformation
As the world becomes more connected, businesses are experiencing a rise in data collection, use and storage. To process this data, new solutions such as cloud and analytics are emerging and transforming business operations. But these changes can also bring increased risk if security is not addressed.
We believe security, privacy and compliance must work alongside transformation, so we built our Advance-6 Bare Metal Servers using Intel® SGX – because it delivers Confidential Computing and increased data protection for our customers. Disk and network encryption can protect data while it is stored or in-transit, but traditionally, data is vulnerable while it is actively in-use inside the CPU and memory. Intel SGX creates hardware-protected “enclaves” designed to shield data and code from unauthorized parties or software while it is in-use. Data and code inside an enclave are not accessible by the cloud administrators or software stack, so your cloud host cannot access your organization’s private data, helping to comply with requirements imposed by GDPR and other regulations.
Rising to the security challenge with Confidential Computing
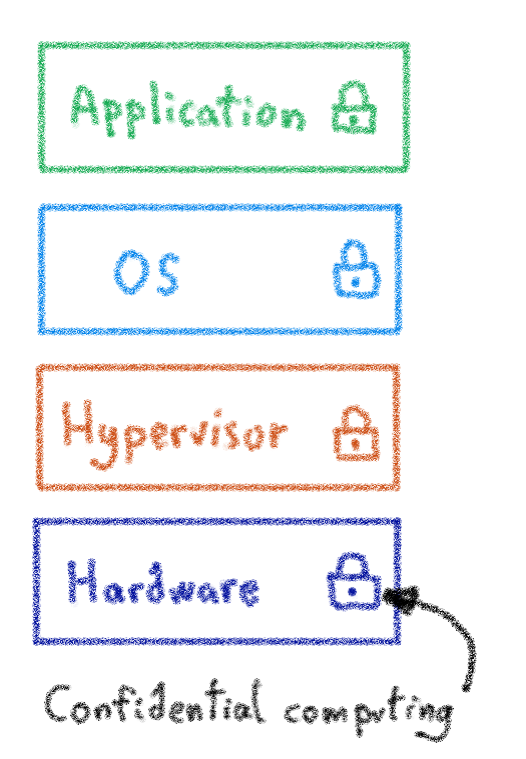
Enterprise data faces an increased threat from hackers, unauthorized third parties and malicious insiders, who often leverage exploits in other applications, or privilege escalations in the OS and hypervisor layers. And as software security improves, attackers have started moving down the stack to identify new vulnerabilities. This puts business-confidential or regulated data at risk. A data breech can result in severe monetary and reputational damage.
All of this means that perimeter defences are no longer enough. What is needed is a multi-layered defence strategy that makes it infeasible to execute a successful attack. Confidential Computing technology has become crucial for such strategies, as it uses a hardware-based approach to isolate data within a trusted enclave and encrypt it in memory. This protects data from vulnerabilities in the OS and hypervisor layers and ensures even users with full access permissions cannot decipher the data without a key.
Confidential Computing is “Compliance Computing”

Europe is setting the pace for the world in privacy and data protection, and organizations that handle personal or regulated data need to take steps to minimize risk of a breech or violation. That means deploying industry best practices and the latest privacy-preserving technology to maintain data security, sovereignty, and control.
Confidential Computing with Intel SGX can be a key part of a compliance regimen and help reduce regulatory risk. Not even a cloud provider like OVHcloud can access the data protected inside an enclave. In addition, OVHcloud offers attestation services so customers can receive cryptographic verification that their workloads are running on genuine Intel SGX hardware, the microcode is up-to-date and the software load is exactly what is expected. Attestation helps assure our customers their data is protected and compliant.
A new level of performance, confidence and security
The Advance-6 Bare Metal Server offers enhanced performance, while enabling solutions to be deployed quickly and at scale. It benefits from PCIe Gen4 and data centre grade NVMe disks, which boost bandwidth, and at the same time, OVHcloud Link Aggregation feature enables the two servers’ physical network links to be aggregated for optimal network speeds.
Advance-6 Servers also contain 3rd Gen Intel® Xeon® Scalable Processors, which improve per-core performance with Intel® 10nm processes. They also contain Intel® SGX – the technology that drives Confidential Computing. Intel® SGX is built-in at the CPU level and enables data to be isolated inside trusted encrypted enclaves.
Intel® SGX also provides:
- Protection against attacks even if the OS/drivers/BIOS/VMM/SMM are compromised
- Increased protection for secrets (data/keys/passwords) even when the attacker has full control of the platform
- Defence against attacks such as memory bus snooping, memory tampering and ‘cold boot’ attacks against the RAM
Examples of Confidential Computing
Here are some examples within machine learning and cryptography:
Secure Multi-Party Compute
Organizations often need to collaborate but sharing data is prohibited due to confidentiality or regulation. Secure Multi-Party Compute is a privacy-preserving technique that enables multiple parties to pool their data and yield more accurate results, whilst keeping each party’s data private from the others. All parties can use the attestation capabilities to verify that their “data clean room” is operating properly and the software is what they expect. Intel SGX is being used today in multi-party medical research and financial fraud detection use cases.
Federated Learning
Federated Learning is a Privacy-Preserving Machine Learning (PPML) method that deploys algorithms to decentralised devices or sites in order to create pooled analysis from data too large or sensitive to move to a common data clean room. In this use case, the algorithm is protected in an Intel SGX enclave while it conducts its analysis. After removing any private information, the results are related to a central node, combined with results from other nodes, and new weights or parameters are pushed to the remote models. This ensures sensitive data is not exposed to threats and helps organizations to build a more accurate model.
Key Management
Key Management is the practice of managing encryption keys, whether that’s generating and storing keys, or replacing keys for users. A common approach is to keep keys separate from data, often with Hardware Security Modules (HSM) – physical hardware designed purely for protecting and managing encryption keys and performing other authentication and encryption functions.
Mitigating data security and compliance risks is a big challenge with high stakes. OVHcloud’s new Advance-6 Bare Metal Servers with Intel SGX can help you rise to that challenge with hardware-based protections that defend your data from threats and help keep your organization compliant with privacy regulations.
Intel® SGX is available with Advance-1, Advance-2 and Advance-6 Bare Metal Servers.
Product marketing manager in charge of bringing to market the latest innovations of OVHcloud Bare Metal Cloud Universe around Bare Metal, Managed Bare Metal and Virtual Private Servers.
