On the 7th of match, VEEAM has released a kb describing a new CVE on several software provided by the company. This vulnerability may result in credentials leak and remote code execution.
VEEAM is a software company specialized in the resilience of virtualization infrastructures and cloud based applications. The principal software, VEEAM Backup & Replication provides a backup solution for virtual machines, physical servers, cloud infrastructure or applications. It supports several types of backup repositories to store backup (CIFS, S3 bucket, …).
VEEAM in OVHcloud
At OVHcloud, there are many ways to consume VEEAM software:
- The first one is the Veeam Backup Managed option of Hosted Private Cloud. OVHcloud fully manage this solution and so, we already applied the mitigation related to this vulnerability.
- The second one is to install a backup server and use the Veeam Enterprise (proposed by OVHcloud) option to get a VEEAM License. In this Option, License is billed with a pay as you go billing. In this configuration you can use all features available in Veeam Backup & Replication and fully manage the infrastructure
- The last one is to install a backup Server and bring your own license. In this configuration you fully manage the backup infrastructure.
In the last two options, you can add Hosted private clouds, dedicated servers and other services in the VEEAM Backup & Replication software.
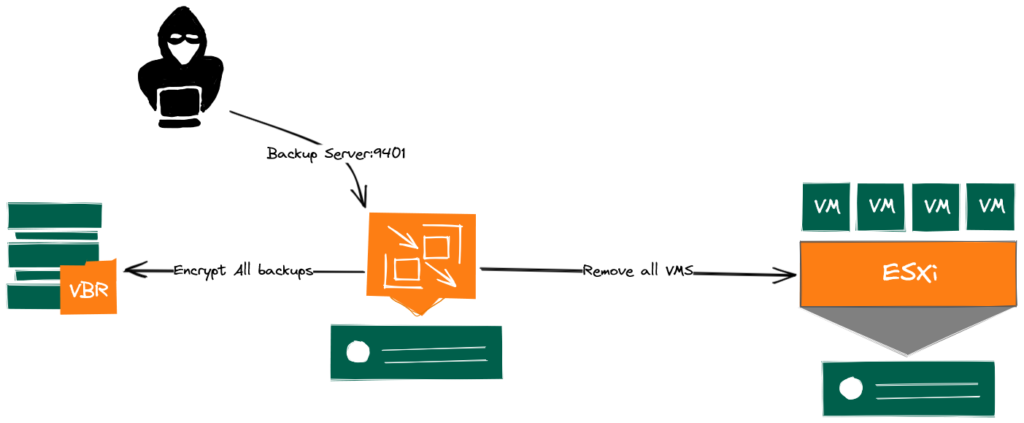
The CVE-2023-27532 affects to Veeam.Backup.Service.exe listening on TCP 9401 port of VEEAM servers. It allows an unauthenticated user to request credentials stored in VEEAM database but also to remotely execute commands on the Backup Server. The Attacker may use those credentials to gain access to any servers protected by the backup software.
Exploit scenario
Even if it is not trivial to exploit this vulnerability, at least one ransomware organization actively exploits it, and many exploit codes are publicly available. Therefore there is a serious concern that automated attacks number increase in the next few weeks.
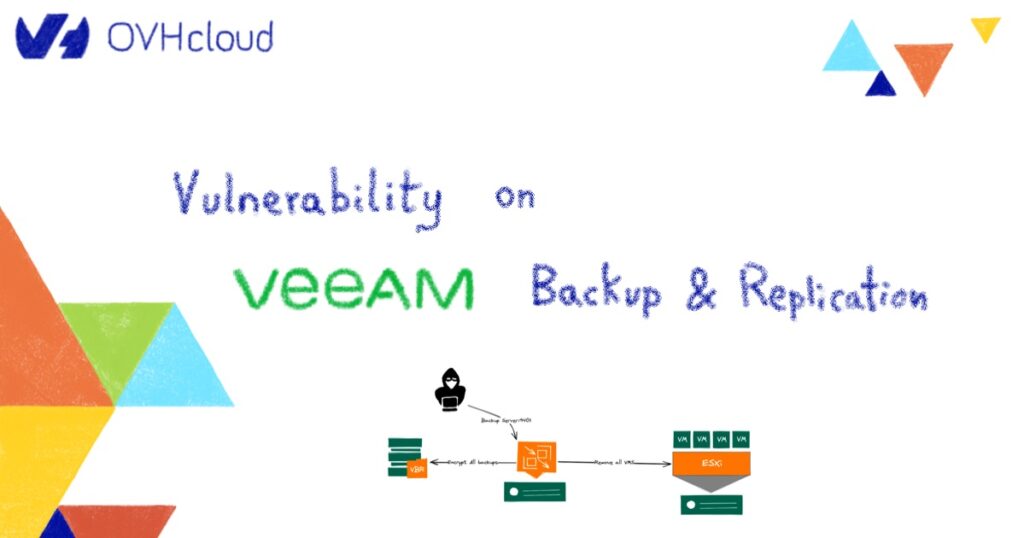
In the operating method observed, the attacker exploits the CVE to get the credentials of the infrastructure covered by the backup solution (ie: vSphere credentials, …) in order to remove all virtual machines from the inventory and finally encrypts all backups. Then, he will ask for a ransom to get the encryption key. For now, we only identified this exploit on Backup Servers or Backup Proxies running Windows operating system where the port 9401 directly exposed on The Internet.
How to know if my server is vulnerable
All Releases of VEEAM Backup & Replication earlier than 12.0.0.1420 P20230223 or 11.0.1.1261 P20230227 are vulnerable. If untrusted IPs can reach the port 9401, the service is vulnerable.
Solution & Mitigation
In order to protect your infrastructure, we highly recommend to update your backup software. You can find patched binaries in the official documentation.
Waiting for the update, and to prevent future vulnerabilities exposition, we recommend to apply the following configuration:
At first, We highly recommend to avoid exposing Backup Infrastructure directly on unsecured networks (Internet, ..,).
When you install VEEAM on a server, it will configure the firewall to allow any connection on VEEAM ports without restriction on Remote address. All ports are so directly reachable from everywhere.
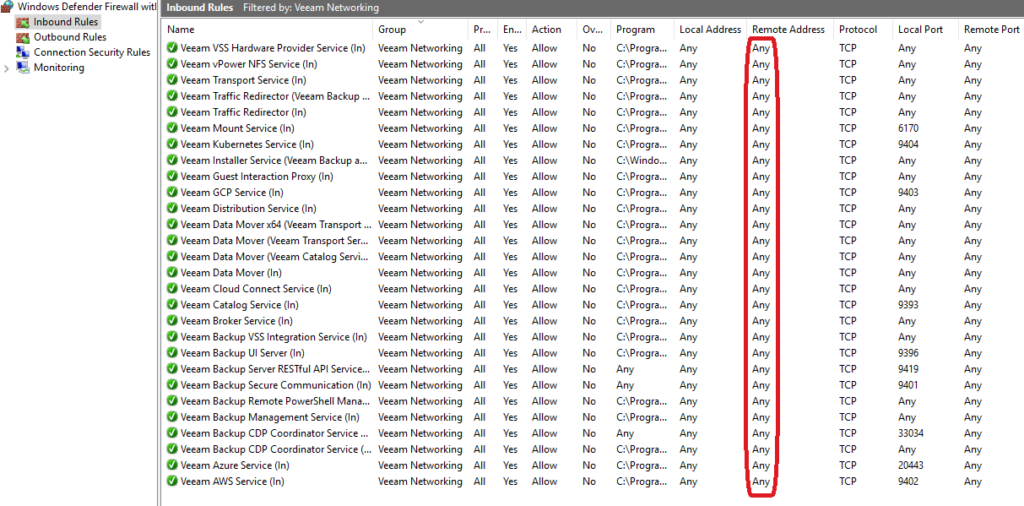
We recommend to apply firewall rules to restrict the ports to the strict minimum of hosts.
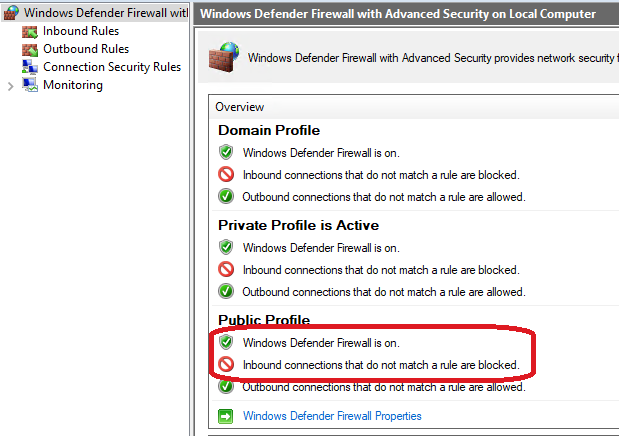
To do so, make sure the Windows Defender Firewall is set to block any inbound connections that does not match a rule.
Then, make sure all ports used are only reachable from servers you trust. For an optimal configuration refers to the official documentation.
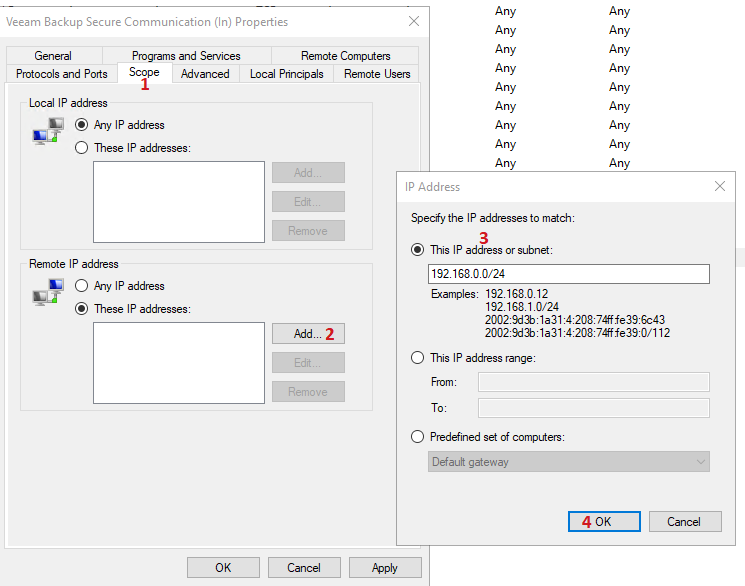
You should see the firewall rule is now restricted to the IPs you configured.
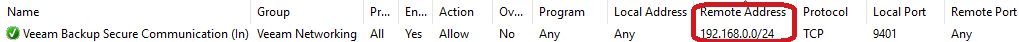
Finally, if you are not using the mount server, we recommend to totally block totally the port 9401.
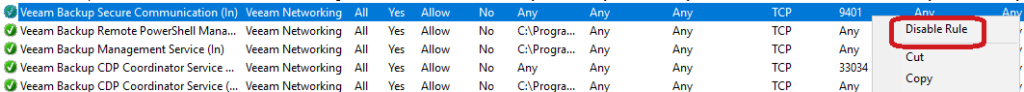
Unfortunately, as the exploit is using legit access, There is no possible mitigation at virtualization infrastructure or backup repositories level. Therefore, It is essential to guarantee the security of components using those infrastructures.
If you get compromised
If you think you have been compromised, we highly recommend to contact OVHcloud support as soon as possible in order to evaluate solutions to maybe recover your data.
Additional links:
https://www.veeam.com/kb4424
https://helpcenter.veeam.com/docs/backup/vsphere/used_ports.html?ver=120
https://www.ovhcloud.com/fr/enterprise/products/hosted-private-cloud/
https://www.ovhcloud.com/fr/enterprise/products/hosted-private-cloud/veeam-backup-managed/
https://www.ovhcloud.com/fr/storage-solutions/veeam-enterprise/
Working on Hosted Private Cloud for more than 10 years, I participated to its evolution, creating managed backup, disaster recovery, and managing the compliance with PCI DSS and SecNumCloud. I'm now in charge of the architecture of the product.

