Confidential Computing
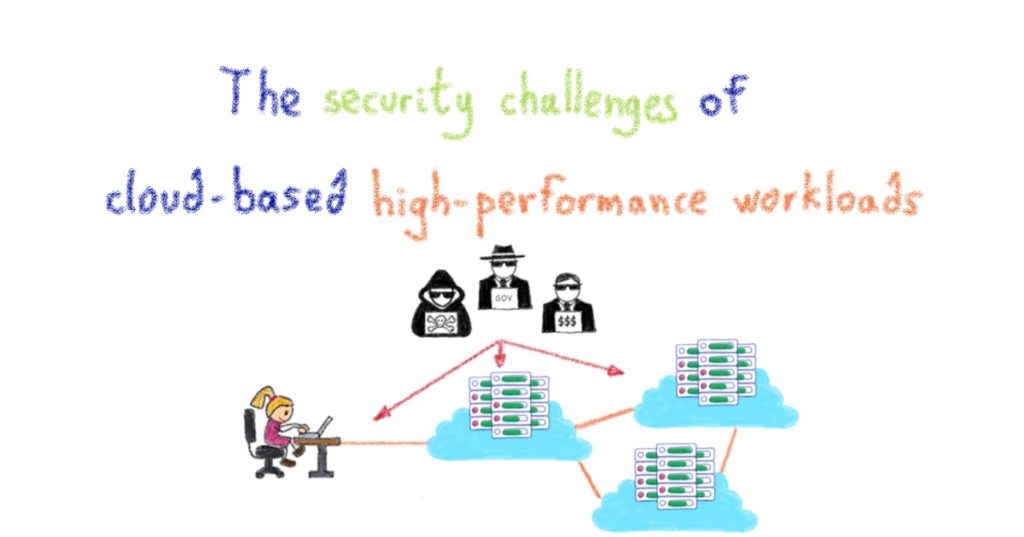
What is Confidential Computing? During the past decades, the IT industry focused on the protection of data which was stored or “on the fly”. Data encryption and decryption is a commodity service and used by almost all users and companies. Well known examples are VPN for secure connections or BitLocker form Microsoft to encrypt storage […]
Confidential Computing Read More »