
In the IT and Tech world, a laptop is key for everyone: this is the device we use everyday. Through this article, we want to introduce the first days in OVHcloud, from a Linux-enthusiast newcomer’s perspective and explain which technical choices have been made for linux laptops by Workstation and Security teams and the reasons behind them. (These laptops are used to manage OVHcloud production and services).
1. Introduction to Linux: Not just for nerds
When I first stepped foot in the OVHcloud offices, I quickly found myself facing an important dilemma: Which operating system to use? Of course, the big three were up for grabs: Windows, MacOS or Linux. Like many of my peers working in the more technical areas of our industry, I was used to using Linux as a server operating system—and to see it as an option for a workstation was a pleasant surprise to me. It’s a rare anomaly that employers would let the crazy tech people amongst them work on the platform that’s so familiar to them; and I was really pleased to be given the opportunity. Soon enough, I had a Linux laptop and a YubiKey plopped in front of me, and some guidance in taking my first steps to set it all up.
To me, there are key reasons why one should choose to work on a Linux workstation—especially in our industry. Aside from the homey familiarity (if you know, you know), there’s the fact that by using what is closer to what you actually deploy on, the more seamless the experience becomes. For example, someone who writes backends will find it easier to weed out the more insidious bugs and weird behaviours inherent to the operating system if they actually write and test their code on that very same operating system. A half-way point to explain this concept could be in using docker containers as development environments – but I am getting too far off topic now.
Anyhow, as I finished following the last steps of the onboarding process, and started to configure this new machine as I would my own – I encountered a sudden a roadblock of a realisation that halted me in my tracks.
“Why can’t I have root on my laptop??? Because—it’s not yours…”
Suddenly, I realise I cannot do anything except installing packages or updating my machine. No root shell to speak of, no privilege escalation in sight…and how sad! This is something I had not considered before while using other operating systems in a business environment: the hardware and the software contained within this Linux are not my own! Though frustrating, I needed to make peace with it and move on. At least I can configure the small user-level stuff, and for the most part, that’s okay… Dotfiles, anyone?
As I make progress with the new machine, I realise there is another benefit of using Linux that I had not considered before—not anything to do with the operating system—but rather a purely social one. OVHcloud has organised a special group of Linux users ready to discuss and help each other out at any moment. This is especially useful when you’re completely new to the professional aspects of using Linux, and the guidance they can offer has come in handy more than once. This aspect is something deeply familiar to people using Linux, or other pieces of software from the free, open-source world. Indeed, I discovered the other people using my same operating system, and through that discovery, I found my community.
Whether you’re new to Linux, or just write your own kernel modules on the weekend, we’d be delighted detail for you the how’s and why’s of using Linux workstations at OVHcloud. We hope this article will both interest and inform you as to how we do things on the Linux Workstation team. I begin by recounting a little bit of history.
2. Linux history

Linux is far from a new thing, but having it on a work laptop is unusually rare—even today. OVHcloud started this crazy Linux adventure back when tower workstations ruled the land. Since then, the landscape of corporate computing has drastically changed, due to major updates to cybersecurity policies around the world, and even a couple COVID lockdowns. It was in this era that began the laptop workstation we use every single day.
To keep things brief, we went through a few key milestones along the way: the configuration of a TFTP server for OS deployments, an initial Puppet setup, and monitoring tools in 2021. The year 2023 saw the Linux community appear on our internal chat service, and we integrated many changes to how we interact with the helpdesk team to improve their service, as well as how we handle their hand-offs. Later in 2024, we improved how we updated our configurations, applying a more developer-focused approach (PR checks, better secrets protection, and more…), and we opened our repository to the Linux community. Most importantly, we successfully passed the PCI-DSS audits! And we’ve got many more exciting things planned for 2025 that we cannot wait to launch. Of course, you’ll see all these in due time. 😉
In our locales across the world today, we count over five hundred machines running an LTS version of Ubuntu that we manage; that number grows steadily as more users join us, expanding the Linux community. Our team has also grown: we are now four Linux nerds, each helping to configure and manage your workstation! However, the Windows and MacOS teams are smaller, despite their workstations making up the vast majority of our fleet today (around 85%). This demonstrates how Linux’s fleet management tools still have a long way to go to be on par with other operating systems—something we’re working hard to improve.
3. Workstation design
One of the most important factors for maintaining a Linux workstation fleet is how you design the infrastructure to support that. The simple architecture diagram below demonstrates the different moving parts and network zones we use to keep things working as they should.
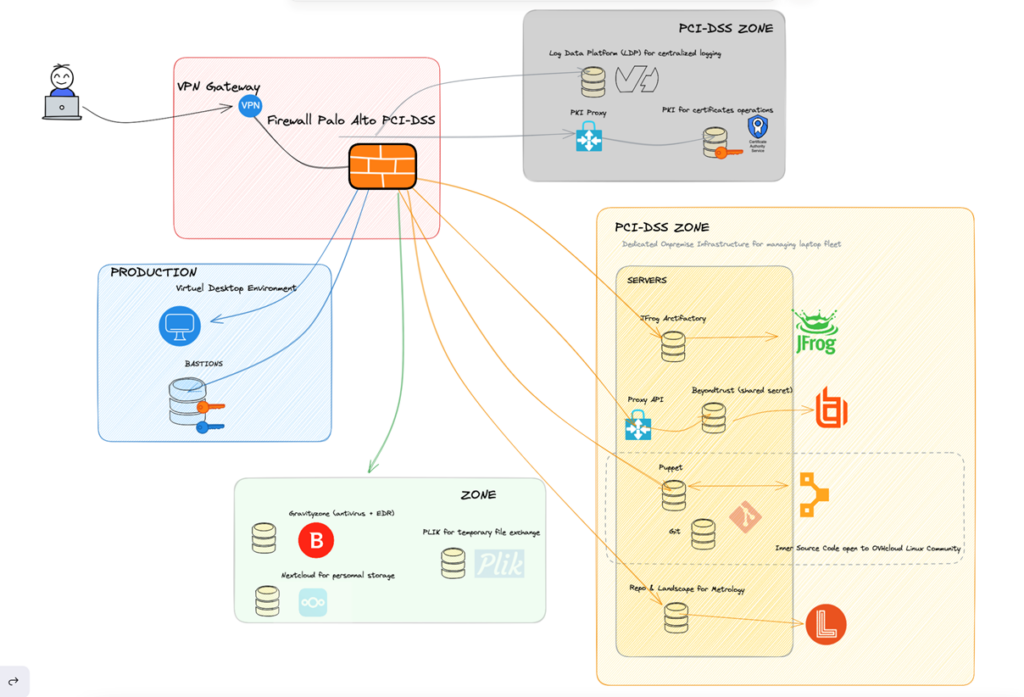
4. Keeping it all together
Puppet, the configuration management system, is of the greatest tools we have at our disposal. Initially intended for server usage, its agent-server architecture works perfectly for a more conventional workstation use case. Puppet enables us to keep a declarative configuration that we store on our Git repo, and allows every Linux user the access to make their own changes through pull requests if needed.
Thanks to Puppet and how it manages its configurations through structured files reminiscent of code—this is Infrastructure as Code, after all—we can work on projects for the Linux workstation the same way a team of developers might work on their codebases. It allows us to make quicker changes safely, and with multiple sets of eyes scrutinising every line of code that’s added, removed, or otherwise modified. Some developer teams might relate—we also divide our work through Epics in a generalised Agile workflow. Most of these Epics track the progress of our improvements on Linux workstations—for example PCI-DSS, and SNC compliance—the goal being to replace Mac SNC in the hopefully nearer future.
Another Epic follows our laptops’ Operating Systems, migrating from Ubuntu 22.04 LTS to 24.04 soon.
We also use Puppet when we need to deploy fixes related to RUN Incidents, or when it impacts all the park, or its majority. The Helpdesk Team handles L1 requests, and we are working on training plans to help them improve too. On our end, we handle every escalated request and incident.
Secure from the ground up
Integrated throughout, we use secure LUKS (Linux Unified Key Setup) to encrypt the root partition of the operating system—this includes all your data as well. To explain it more simply, LUKS is a block device encryption standard and tool set initially created in 2004. It provides file system-agnostic encryption with multiple ways—up to 32 keys—of decrypting partitions, helped by a header located at the start of the encrypted blocks. Upon provisioning, the HelpDesk member creating your workstation ties your YubiKey to one of the key slots on the root drive, giving you a physical key to decrypt this digital lock. Encrypted disks ensure that in the unlikely event of a theft or loss, your data stays absolutely unreadable in the hands of a malicious actor. It’s also part of the PCI-DSS compliance.

5. Keeping security tight
Obviously, one of the most important facets of configuring and managing hundreds of Linux laptops is security. Within our workstations, Payment Card Industry’s Data Security Standard (more commonly known as PCI-DSS) is paramount to security. Its strict nature ensures that our attack surfaces stay small and sparse, guaranteeing more peace of mind when it comes to operational security at OVHcloud. If you’re unfamiliar with PCI-DSS, its origins are simple: PCI-DSS comes from an industry-led data security council whose mission is to gather feedback from the payment card industry and create security standards around that. Now, applying PCI-DSS is a whole other story, one that we’ve fought hard to put in place. And we’re happy to say that—barring a couple of unavoidable exceptions—we follow the PCI-DSS as closely as we possibly can.

To keep this in line with our commitment to safety, we have deployed the CIS benchmark best practices on all laptops. Based on a consensual effort of global cybersecurity experts, these directive configuration recommendations help to more confidently protect our systems against threats. Amongst additional protective measures, OVHcloud also installs Bitdefender on each operating system upon its first set-up.
Finally, in the future, we plan to export auth logs to an internal service—both to enhance observability and to enable us to keep a digital eye on possible intrusions from inside the network.
6. Keeping things open
OVHcloud Linux users are admittedly demanding about their laptops and the tools they use on a daily basis. That’s why we decided to create an internal Linux community with an inner source approach. Indeed, it’s not easy to purpose technical tools to technical specialists, so our strategy is most importantly to, “Keep things open and together!” To avoid frustration for users, we find the need to explain our thought processes and our decisions (sometimes having resulted from non-conformity on an audit). All of us in the team remember at some point when we had to reduce size of a bash_history file—a true nightmare for users—and for us! The main thing you learn from such a situation is, “Don’t apply changes without communicating and think about all it impacts, even if it is related to a non-conformity.”
This is exactly why one of the main goals of the community is, “Don’t hesitate to participate!”
We believe that communication is key for our users, and we are sure everyone can impart ideas to improve our laptops. The code we use to manage the fleet is open and reachable by every Linux user in our stash repository—meaning that everyone can see how we design our code, and can submit pull requests if need be. In the spirit of open-source and in the search for transparency, we intend to keep things open for our users, especially when it comes to the machines they work on each and every day.

This community-centred approach has changed a lot of things, most importantly when it comes to matters of transparency: we communicate about strategic decisions, about the changes to come, and about the impacts from these changes.
We have created a dedicated internal discussion channel including all Linux users of the company. Many topics are shared here: innovation, tools, issues, problems, the future… We sometimes hear about frustrations and misunderstandings, but we are proud to say that, nonetheless, is one of the most popular spaces in the company. Welcome to Linux.
We hope you found this article interesting. This is just the first article in a series where we will go more into details on the technical choices implemented and their consequences.
